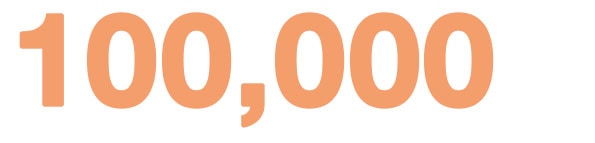Cybersecurity has become a big, if not the biggest, topic in the IT world. High-profile ransomware attacks like the Colonial Pipeline, Kaseya, and the Pegasus spyware hack have dominated news cycles throughout 2021. But just how important is cybersecurity to your business? After all, your business looks nothing like these notorious companies. We’ve put together ten of the most important cybersecurity stats to know to illustrate that cybersecurity matters no matter the size or industry of your organization.
1. The world faces over 100,000 malicious websites and 10,000 malicious files daily
When faced with this many websites and files daily, all aimed at compromising your personal data, having the knowledge to tell when something is wrong is key to your cybersecurity. To combat the wave of files and sites aiming to compromise your vulnerability, top organizations are investing in cybersecurity training. This training extends beyond just keeping the IT team up to date. It means equipping everyone in the organization with the tools to identify attacks like phishing scams, and understand escalation procedures when they are compromised.
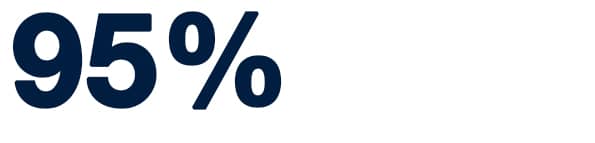
2. 95% of cybersecurity breaches are caused by human error
It’s easy to think you won’t be the cause of a breach because you have antivirus software on your computer and use a password more complex than “password123,” but research has shown that an overwhelming number of breaches are caused by human error, not vulnerabilities in software. Ensuring you are following best practices for cybersecurity and, again, staying on top of cybersecurity training will go a long way to keeping not only your information but your organization’s, safe from a cyberattack.
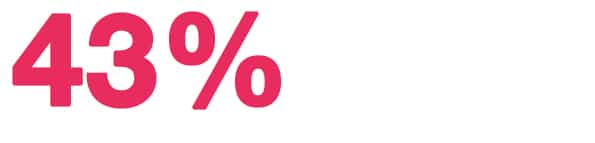
3. 43% of cyber attacks target small businesses
The size of your business really doesn’t make a difference to a hacker. In fact, smaller businesses are often targeted instead of large organizations as they often have more vulnerable systems and fewer protective measures in place. Ensuring your organization’s cybersecurity holds up to industry best practices is important no matter your size or finances.
Want to see how your organization stacks up against the best? Invest in a cybersecurity audit from Tech Superpowers to see how protected you are and get concrete steps you can take to improve your readiness.
4. Since the beginning of the pandemic, the FBI has reported a 300% increase in reported cybercrimes
Covid-19 has changed our work lives in more ways than just flexible work environments. It has also drastically increased the number of reported cybercrimes. While people were learning how to use Zoom and figuring out how to work remotely for the first time in their lives, hackers were amping up their attacks, preying on the average internet user when they were the most vulnerable.
5. The average cost of a data breach is $3.86 million
From lawyer fees and data recovery costs to patching lapsed infrastructure and reputational damages, a data breach can be quite costly, even devastating to an organization. Beyond just the staggering cost, a data breach is not a quick fix. The average lifecycle of a data breach is 280 days from identification to containment, requiring businesses to lose almost an entire year on a breach when they could be focused on other things.
6. $17,700 is lost every minute due to phishing attacks
Phishing attacks remain one of the most popular methods of attack by cyberattackers, and in recent years spear phishing (a more targeted form of phishing) is on the rise. While phishing emails are relatively easy to spot to the well-trained eye, spear phishing is a bit more difficult to identity. Aaron Higbee, CTO of anti-phishing firm Cofense defines it as “a campaign that was purposefully built by a threat actor with a goal of penetrating one organization, and where they will really research names and roles within a company.” Unsure if that email request from your boss is legit? A call or text to confirm can go a long way!
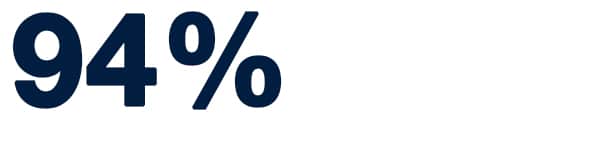
7. 94% of malware is delivered via email
Rather than coming from social media, new software, or other sources, most malware is transmitted via email. Phishing is a popular way for attackers to not only steal your personal information but covertly deliver malware to your device. Once on your device, malware spreads throughout your computer and even across networks.
Want to learn more about preventing phishing scams? Check out our article How to Spot a Phishing Email for more information.
8. Only 16% of executives say their organizations are well prepared to deal with cyber risk
Being prepared for cyber attacks takes more than having a dedicated IT team. It requires organization-wide buy-in, from top to bottom. From training to collaboration on policy implementations, keeping your organization on top of the ever-evolving landscape of cybersecurity is a team effort.
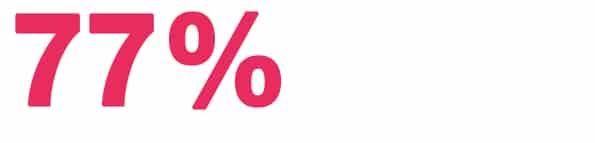
9. Over 77% of organizations do not have a cybersecurity incident response plan – source
We all remember our school days where a few times a semester we would be dragged out of our classrooms to stand outside for 30 minutes or so to test our school’s readiness for a fire. While most of us enjoyed these short windows to be outside and take a break from school for a few minutes, they were essential for teachers and staff to be prepared when disaster does strike. By applying this same logic to incident response with cyberattacks, organizations can limit the scope and overall damage when disaster strikes.
10. Ransomware attacks happen every 11 seconds, up from 40 seconds in 2016
Just as phishing scams are on the rise, so too are ransomware attacks. Not only are ransomware attacks on the rise, they are also evolving in their tactics. In the past, hackers would take your data, encrypt it and sell it back to you. As the average user has learned not to trust a hacker trying to sell their data back to them, they have begun to bypass the user entirely and sell the data to third parties. Learn more about how ransomware has evolved by reading our article on the 5 Biggest Takeaways from the IT Nation Secure conference.